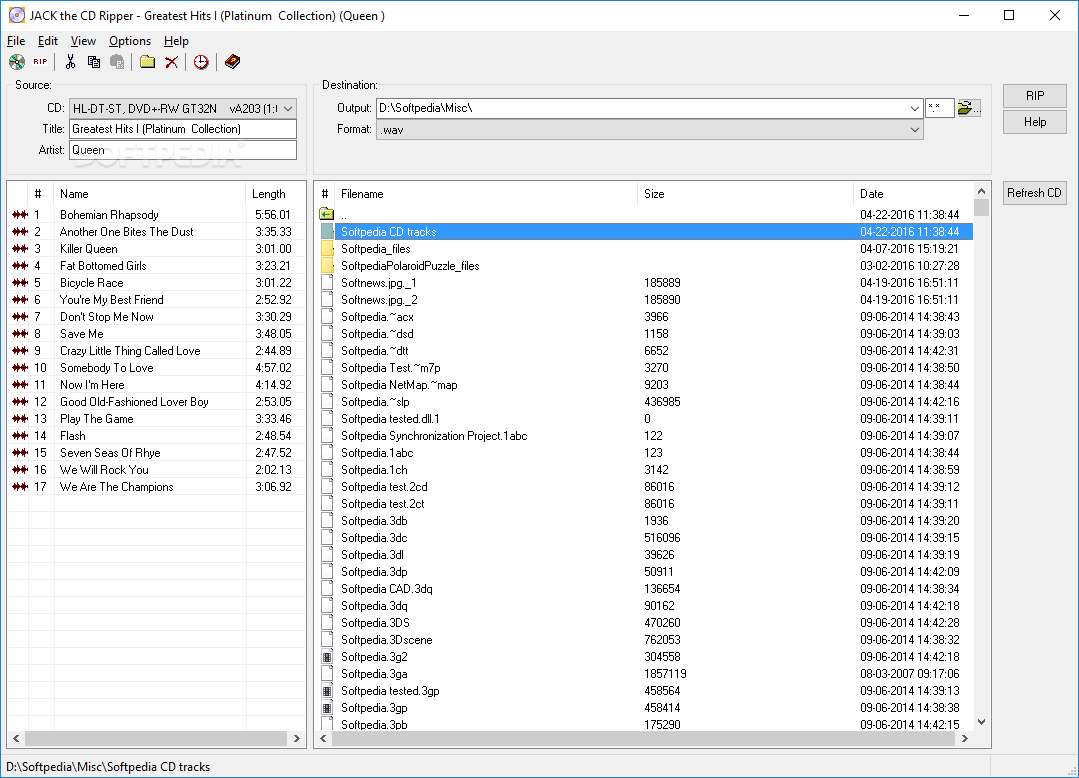
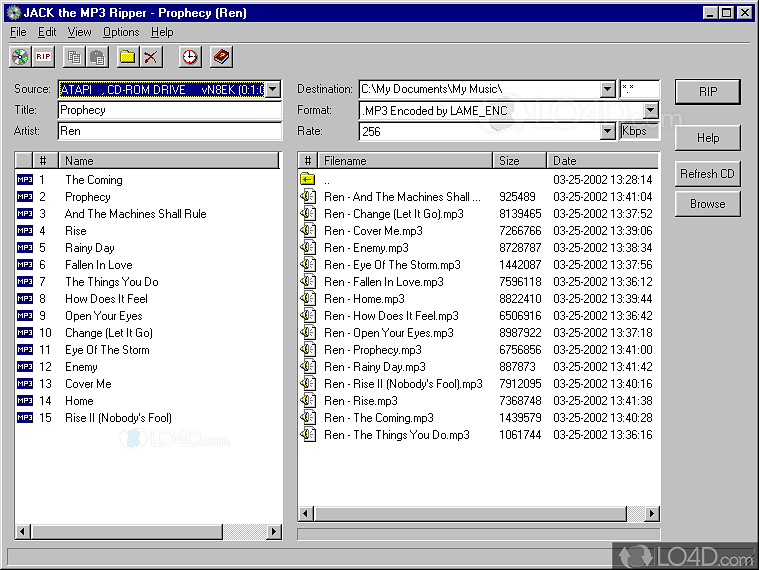
Beginners Guide for John the Ripper (Part 1) June 5, 2018. November 19, 2020. We know the importance of John the ripper in penetration testing, as it is quite popular among password cracking tool. In this article, we are introducing John the ripper and its various usage for beginners. To verify authenticity and integrity of your John the Ripper downloads, please use our GnuPG public key.Please refer to these pages on how to extract John the Ripper source code from the tar.gz and tar.xz archives and how to build (compile) John the Ripper core (for jumbo, please refer to instructions inside the archive). This video shows how to download and install John The Ripper on windows.Download John The Ripper: www.openwall.com/john/Music information:Jarico - Island.
John the Ripperis a fast password cracker, available for many operating systems.Its primary purpose is to detect weak Unix passwords,although Windows LM hashesand a number of other password hash types are supported as well.John the Ripper is free and Open Source software,distributed primarily in source code form. John the Ripper Pro builds upon the free John the Ripper to delivera commercial product better tailored for specific operating systems.It is distributed primarily in the form of 'native' packages forthe target operating systems. |
|

John the Ripper Pro is currently availablefor Linux on x86 and x86-64 (x64) systems,with support for the latest Intel and AMD processor features such as SSE2,andfor Mac OS X on both Intel and PowerPC Macs,making use of SSE2 and AltiVec acceleration, respectively.
Jack The Ripper Hacking Software
Proceed to John the Ripper Pro homepage for your OS:
- On Windows, consider Hash Suite(developed by a contributor to John the Ripper)
Support for certain other operating systems and processor architectures isplanned.If your OS is not supported yet,please use the Quick Comment field at the bottom of this web page torequest support for your OS;be sure to explicitly indicate your interest in purchasinga copy and license, and provide your e-mail address and desired price.Please note that support for a new OS in Pro versions ofJohn the Ripper may only be added in response to commercial demand.Meanwhile, feel free to explore thecross-platform and free version of John the Ripper.
John the Ripper Procurrently supports the following password hash types(and more are planned):

- Traditional DES-based Unix crypt(3) -most commercial Unix systems (Solaris, AIX, ...),Mac OS X 10.2, ancient Linux and *BSD
- 'bigcrypt' - HP-UX, Tru64 / Digital Unix / OSF/1
- BSDI-style extended DES-based crypt(3) - BSD/OS, *BSD (non-default)
- FreeBSD-style MD5-based crypt(3)- older Linux, FreeBSD, NetBSD, Cisco IOS, OpenBSD (non-default)
- OpenBSD-style Blowfish-based crypt(3)- OpenBSD, some Linux, other *BSD and Solaris 10+ (non-default)
- SHA-crypt (sha512crypt and sha256crypt) - newer Linux
These are supported when running on a Linux system with glibc 2.7+ (any recent system) - Kerberos AFS DES-based hashes
- LM (LanMan) DES-based hashes -Windows NT/2000/XP/2003, Mac OS X 10.3
- NTLM MD4-based hashes -Windows (all versions)
- Mac OS X 10.4 - 10.6 salted SHA-1 hashes
- Mac OS X 10.7 salted SHA-512 hashes (new in 1.8.0 Pro, currently available for Linux only)

You can browse the generic documentation for John the Ripper online.Also relevant is ourpresentation on the history of password security.
Jack The Ripper Hacking Software
743211 |
Comments are closed.